
If the YubiCloud is not to be used for the validation of Yubico one-time passwords (OTP), validation servers can also be managed in-house. In principle this is not very difficult, but the redundant setup is rather poorly documented. 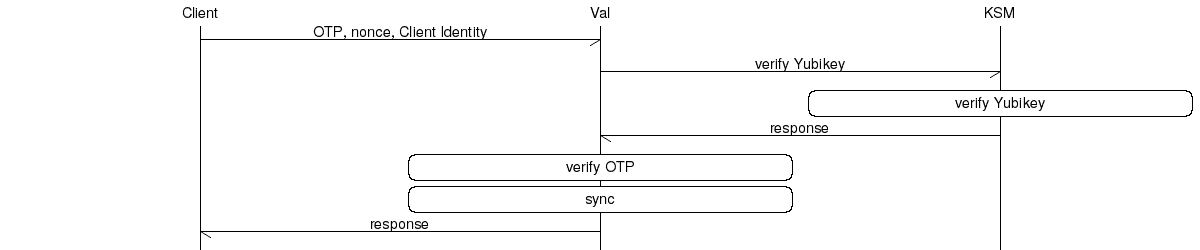
MySQL is used as the backend and Apache as the frontend. The two components yubikey-val and yubikey-ksm are simple PHP applications, which consist of just a few files. 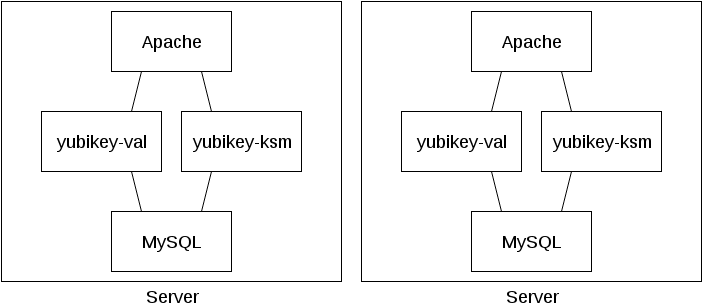
Apache, PHP and MySQL should be installed first. Due to the packet dependency of yubikey-ksm and yubikey-val, a MariaDB server cannot be used. Then, two databases should be created (ykksm and ykval) with associated users (ykksm_reader and ykval_verifier).
The individual Yubikeys, that is to say all data (incl. the secret AES key) of all Yubikeys, are recorded in the Yubikey key storage module (KSM). The service can be used to verify whether a Yubikey with an associated one-time password (OTP) is valid, but not whether it is a replay attack. As the software does not have a mechanism to synchronise the servers, this is resolved via a MySQL master-slave setup. Corresponding instructions on how this can be done is available, for example, on DigitalOcean. It must be noted that only the ykksm database should be synced (binlog_do_db = ykksm).
On a Debian yubikey_ksm can be easily installed via apt install yubikey-ksm. The configuration of the Apache and the database is then already completed. If the configuration is to be changed afterwards, the corresponding files are located in /etc/yubico/ksm/. More detailed installation instructions can be found at Yubico.
Apache is configured so that there is a global alias /wsapi/decrypt as /usr/share/yubikey-ksm/ykksm-decrypt.php. If there are several VirtualHosts present on the Apache, these should be deactivated in the configuration and only the VirtualHost required for yubikey_ksm should be activated.
New Yubikeys can be created using the ykksm-gen-keys tool. This results in the following output:
$ ykksm-gen-keys 1
1,cccccccccccb,42e31d069785,cf00b1f4c2c80e395b5e7532a5929cba,d05f7e394f0e,2016-03-22T13:12:25,
The yubikeys table is present in the database. This has the following schema: ```SQL
CREATE TABLE yubikeys (
serialnr int(11) NOT NULL,
publicname varchar(16) NOT NULL,
created varchar(24) NOT NULL,
internalname varchar(12) NOT NULL,
aeskey varchar(32) NOT NULL,
lockcode varchar(12) NOT NULL,
creator varchar(8) NOT NULL,
active tinyint(1) DEFAULT '1',
hardware tinyint(1) DEFAULT '1',
PRIMARY KEY (publicname),
UNIQUE KEY publicname (publicname)
) ENGINE=InnoDB DEFAULT CHARSET=latin1;
If new Yubikeys are to be created and stored directly in the database, this can be implemented with the following script: ```Bash
#!/bin/bash
MYSQL='mysql'
NEXTID=$(echo "SELECT t1.serialnr + 1 FROM ykksm.yubikeys t1 WHERE NOT EXISTS (SELECT serialnr FROM ykksm.yubikeys t2 WHERE t2.serialnr = t1.serialnr + 1) LIMIT 1;" | $MYSQL | tail -n 1)
if [ -z "${NEXTID}" ]; then
NEXTID='1'
fi
KEY="$(ykksm-gen-keys ${NEXTID} | grep -v ^#)"
IFS=',' read -r -a ARR
We use cookies to ensure you get the best experience on our website. By using our site, you agree to our cookie policy.